This guide, originally written for Teslacrypt, has proved to be of some use to other ransomware as well, for example AVADDON (.avdn)
I add the following information, specific to the AVADDON virus:
- There is NO way to recover files, given the methods used to encrypt them (any updates will be written in this same article)
- DO NOT PAY, because it appears that the criminals DO NOT give the unlock code, it seems that it really does not exist and the criminals are NOT found in any way
- News 10th June 2023: found and tested this EMISOFT AVADDON DECRYPTER. It works, when you start let it look for the key for a "long" time (maybe more than 10 minutes)
Ransomware Infection
Let's start by establishing how you got the ransomware. The most known and used infection mechanism is the sending of a false email in which, in some way, you are invited to click on an attachment. And there are many ways to hide malicious code in an attachment, one of them is to send a zipped file which contains inside a js file (javascript) having the same name. This way it runs right away, and you're already screwed!
Windows 10 has protection against encryption, I invite you to search for it on google, this same site has a search box.
Always install and keep good antivirus software up to date. AVG / AVAST are free and work. Alternatively: Kaspersky.
How to avoid virus infection
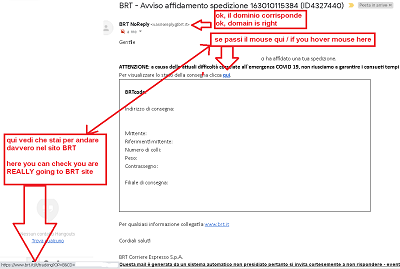
- Before clicking anything, especially in emails, you must hover over it with the mouse cursor, in the lower left corner, in the status bar, the TRUE NAME of the file you are about to click will appear.
- NEVER CLICK on an attachment or link in a mail if you are not absolutely sure what you are doing. EXAMINE IT FIRST
- If you want, you need to download the attachment (⇒ right click → download / save as) and then scan for viruses (⇒ right click on the file → scan with antivirus / scan with AVG etc ..
Here are three examples of link control, with the mouse hover technique:
----------------------------------
----------------------------------
I repeat that the MOUSE HOVER control technique is important and effective for fighting at least 95% of threats!
Always do regular backups on external HDD and keep it away from your PC
Of course, you have to DEACTIVATE the "hide extensions for known file types" option. Because you want to see ALL the extensions. Just to avoid the most banal method of infection: the double extension. Yes, just send you a file like this photo.jpg.exe, and the option will only show you photo.jpg, you will believe it is a jpg (error 1), double click (error 2) and you will be fucked!
Here's another way to check an email:
Payout ransomware: what to do immediately
If a ransomware warning appears on the screen, that is, a message telling you that your files have been encrypted and that to get them back you have to pay a ransom, here's what you need to do immediately:
IMMEDIATELY TURN OFF YOUR COMPUTER !!
YES, I said immediately, in this moment, NOW! DON'T WAIT!!
(you will return to this page from another PC / Tablet / smartphone, as you like, but KEEP THE INFECTED PC OFF !!)
The typical infection mechanism is as follows: the virus infects the PC, encrypts all your files, then creates the payout, and then deletes your original files. That's why you MUST shut down your PC right away: your files may still be there, deleted, but not permanently.
Recovery of files encrypted by ransomware (summary):
- Create a Bootable USB key with a linux distribution
- Start infected PC from linux's USB
- With file manager, check for what extension has been given to files, to find out what's the ransomware
- es: file xxxxx.jpg.avdn ⇒ you've been infected by AVADDON
- look out in web if any solution is given
- example: TESLACRYPT RECOVER by ESET
- Connect an external HDD to the infected PC
- install and run FOREMOST for the recover
- run PHOTOREC for the same reason
So, get a different PC to access the internet, a USB of at least 16GB (8 are enough), an external disk (or a second USB stick) of adequate capacity, to save any recovered files.
1) Create a bootable USB linux
I suggest to use SARDU Free, click here per andare alla pagina download SARDU.
Download it, install it, follow the instructions to create a bootable USB, of at least 16GB, and which contains: Kali linux + Kubuntu linux + Kaspersky LIVE ANTIVIRUS CD + AVG LIVE antivirus CD, all instructions are on the SARDU website and / or in the program itself .
Other method:
Download Kali Linux choose the one suited for your PC, nowadays all PC should be at 64bit
Download Linux Live Usb Creator
Install Linux USB Creator on the SECOND PC, of course, and use it, following the instructions, to create a bootable USB with Kali LIVE linux
At this point you should have a bootable USB stick with Kali on board.
2) Booit infected PC from USB
Insert the bootable USB stick, with the PC off. Turn on your PC to boot from the stick, there are two ways:
1) Enter the BIOS immediately and set BOOT from "removable device" or other similar wording (USB Legacy, USB HDD ... or other)
2) repeatedly press, at startup, the key to enter boot mode (F8, or F12, but the best way is to search the internet for "boot mode" and the name of your PC if notebook, or motherboard, if you have a desktop PC)
Once started, if you have used SARDU you will have to choose → LINUX menu and then choose → Kali, if you have used LiLi USB you will be directly at the Kali screen.
In Kali, the first choice to make is "LIVE", or "TRY". or - better - FORENSIC.
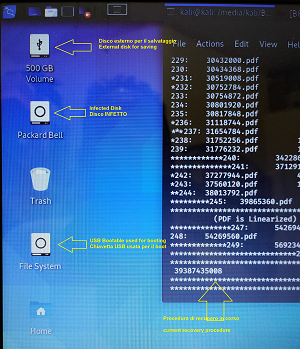
Then you will find yourself at the kali desktop, on the left there should be the hard and removable disks.
Since one will be the external disk for saving, and one will be the disk of the infected PC, it will be good to mount them both (right click → Mount)
3+4) Examinate ransomware and search for solutions
Double click on the disk of the infected system, to examine it, look for a file of yours, and check what the extension is. Just go to the Documents folder or the Pictures folder, which you will find in C: \ users \ yourname \; for example: let's say that your invoice.doc document has become invoice.doc.avdn. You will search on the internet for "avdn extension" and find out that it is the AVADDON virus, if it were invoice.doc.micro, searching for "micro extension" you would discover that it is the TeslaCrypt virus.
At this point I suggest checking if RELIABLE solutions exist. Which are NOT generic antimalware, or purely descriptive articles like I found when looking for Avaddon. NO! I mean serious programs written specifically for the virus, and - in particular - for the recovery of files, therefore a specific decryptor. Otherwise, the risk is to lose ALL your files, so it is better to continue following my instructions.
5+6) Recovery of files encrypted by ransomware
Usually ransomware first encrypts your files, and then deletes them. Deleted files CAN BE RECOVERED, as long as you don't overwrite them, that's the reason for my warning NEVER TURN ON YOUR PC INFECTED by ransomware. This, therefore, is not the decryption procedure, but the procedure for recovering deleted files. Cross your fingers and let's go.
If you have not already done so, connect the external disk to the infected PC, on which, as mentioned, the live version of Kali is running. Mount it (right click + mount).
Launch a terminal, you see it in the desktop image above, it is the 4th icon at the top from the left. Install FOREMOST, typing the following command, followed by enter:
sudo apt-get install foremost
Foremost is a program to recover deleted files, here is its syntax:
# foremost [-h|V] [-qv] [-t type1,type2...] [-s num] [-i ] [-o ] \ [-c ] [] ....
-h Print the help message and exit
-V Print copyright information and exit
-v Verbose mode
-q Quick mode. Search for the header only at the beginning of the sector
-i Reads the files to be analyzed in the folder passed as a parameter
-o Set the directory where the recovered files will be saved
-c Set the configuration file to be used
-s Skip the specified number of bytes before starting the search
-n Extract files without adding the extension
-t Lists the file extensions to be recovered
With the command lsblk or fdisk -l find the name of your infected disk, which will be something like /dev/sd .., in the output of the same commands you will also find the mount point of the external disk, something like /media/kali/B8 ..... In short, you will have to get to an output like this:
This is the case I am dealing with, and which is the basis of this article, /dev/sda is the infected PC disk, you can recognize it by the name and partitions that are typical of windows, the one that interests me is /dev/sda3/
dev/sdb1 is obviously my SARDU stick (it's 32GB)
/dev/sdc1 is the only partition on my external drive, mounted in / media / kali / B8 ...
Well, we have everything we need to run the "magic" command:
two premises: the command should work immediately, and save everything it finds as extensions, that is, what follows the "-t" option, creating a recover folder, containing a folder for each extension.
sudo foremost -v -q -t jpg,png,ole,pdf -o /media/kali/B8D8BD65D8BD2314 -i /dev/sda3
-o = where to save // -i = where to search for things to save // -t ole = stands for the Microsoft OLE format, so, if possible, it will recover Word, Excel and Powerpoint documents
It's not an exact science, so it's possible that something doesn't work, that the command doesn't start or that you can't find anything, in this case we have something to try:
Try to become superuser and give yourself ownership of the disk to read, with the following commands:
sudo chown root /dev/sda3
sudo su
And try to run the above command.
Or try foremost with one extension at a time:
create a folder for each extension, to do it quickly:
mkdir /media/kali/B8D8BD65D8BD2314/pdf_recover
mkdir /media/kali/B8D8BD65D8BD2314/doc_recover
etc..
and the run the command once per extension:
sudo foremost -v -q -t pdf -o /media/kali/B8D8BD65D8BD2314/pdf_recover -i /dev/sda3
sudo foremost -v -q -t doc -o /media/kali/B8D8BD65D8BD2314/doc_recover -i /dev/sda3
etc..
7) Photorec
Try photorec too, it's another program for recovering deleted files. You have just to type photorec in a terminal, give "enter" and follow instructions.. Remember to save all recovered files onto the external HDD, as above.
That's all, recovery depends on how deleted files have been damaged / overwritten, but it's definitely better than nothing.
Once this is done you have to clean up your PC.
Always with Kali I advise you, if you can, to save the encrypted files on the external disk as well, as they are, obviously those that you would like to recover one day, and those that have not been retrieved from the files deleted with the procedure above.
Remove the external disk.
At this point, if you have used SARDU you have two live antiviruses to run on the PC to "clean up", repeat the Boot procedure, and choose "antivirus menu".
Otherwise, extract USB stick and run Windows in safe mode (safe mode instructions) (or press F8 key repeatedly at boot) then run your antivirus.
My best advice, anyway, is to re-format all, and - BTW - set up things like I said in this artcle.